YET ANOTHER WEB AGENCY BREACH – THIS TIME IT’S MAGECART AND YOUR PRIVACY
A stealthy supply-chain attack has compromised more than 30 websites—including a credit union—via malicious JavaScript implanted through a web development company’s templates. But this isn’t your typical Magecart campaign: rather than targeting just payment cards, the attackers exfiltrate broad form and all site data. Furthermore, the stolen data is hidden inside image filenames sent, a surprisingly sophisticated method designed to evade detection.
Attack details: A devious loader and data leaked in chunks through image file names
The attack begins with a loader stealthily injected into the victim’s websites; not via a <script> tag, but through an unusual <style onload=”…”> element, masquerading as a CSS. This evasion technique bypasses traditional scanners.
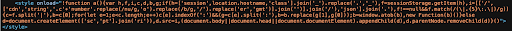
Once executed, the loader retrieves and runs an obfuscated payload from attacker-controlled domains (e.g., cdnstring[.]com, object[.]fm) or uses a cached version from sessionStorage , further reducing the footprint.
The core payload captures everything: form inputs (including hidden fields), cookies, site state, and internal tokens—suggesting a motive more aligned with industrial espionage than classical Magecart card skimming, and likely breaching privacy laws.
Instead of using POST or XHR (which might trigger alerts), the stolen data is broken into chunks, encoded, and exfiltrated via requests for .png, .gif, or .jpeg images, each filename carrying hex-encoded data. These image GETs bypass CORS checks and blend in with normal traffic, making detection extremely difficult.
The Fourth Vendor Breach in Recent Months
This is the 4th time in recent months that Source Defense has identified a software company distributing an infected template that results in Magecart-style implants across their customers’ sites. Two of them attacked US-based agencies while the other two attacked UK based ones.
See links below to the three other articles published:
- Orchestrated magecart attack hits 35 U.S. websites built by the same company
- When Your Trusted Vendor Becomes the Threat
- Multiple websites breached through compromised hosting service
How does Source Defense protect against this attack
Source Defense’s proactive client-side security platform neutralizes threats like this in multiple ways. Our behavioral engine detects and blocks scripts attempting unauthorized form access, data capture, or exfiltration; whether they originate from a third-party domain or are embedded using deceptive tricks like style tags.
Remote scripts from attacker domains such as cdnstring[.]com or object[.]fm are automatically blocked for customers using the Protect product. Additionally, our platform prevents execution of unknown or obfuscated code by enforcing real-time script isolation policies, stopping zero-day threats before they’re known publicly.
How you’d be alerted
If this campaign were active on your site, Source Defense would detect and alert on key behaviors, including:
- Accessing PCI or PII data
- Loading scripts from blacklisted domains
- Sending data to blacklisted domains
These alerts would be prominently displayed in the notification center, dashboard summary, and script behavior widgets, with red flags marking all suspicious activity.
Key takeaways
This campaign highlights how a single compromised software vendor can silently infect dozens of client websites, leaking sensitive data far beyond payment fields. With stealthy vectors like sessionStorage, style tag loaders, and image-based exfiltration, traditional tools like CSP or code reviews simply won’t catch it.
Only real-time, behavioral-based client-side protection can detect and block these sophisticated threats—before your site and your users are compromised
