WHEN SHIPPING POLICIES SHIP A MAGECART ATTACK
The Source Defense Research team uncovered one of the most precisely aimed Magecart loader campaigns seen, where attackers have taken hiding-in-plain-sight to new levels. Instead of injecting obfuscated code across a site, the malicious payload was cleverly embedded inside a shipping policy text field, which is naturally rendered only on the checkout page as part of the normal site flow. This attack requires zero context-checking logic, making it elegant, effective — and dangerous. This GTM and domain was already flagged by the research team last year, as you can see on our X/Twitter feed. What’s new is the clever method in which it’s hidden.
Attack details
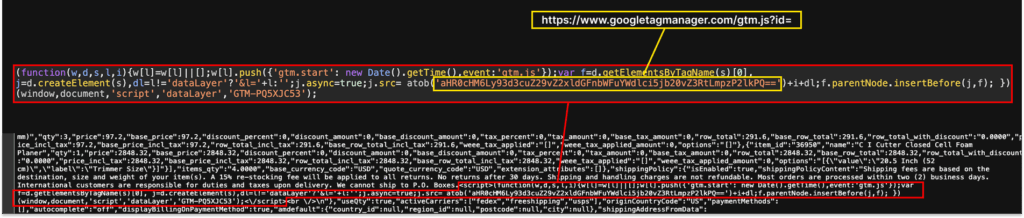
The malicious code was tucked inside a string named shippingPolicyContent, designed to appear as typical shipping language. As displayed in the image below, within it, is a script tag that loads GTM container GTM-PQ5XJC53, shown as obfuscated. The GTM container then injects the skimmer from reviewgatherer[.]com.
Since it’s embedded inside a shipping policy text field, the content is only loaded via a jQuery .html() call on the checkout page. The attacker doesn’t need any conditional logic or obfuscation to check the URL or DOM structure. It’s perfectly scoped by the website’s own logic; no attacker-added conditions required.
How Source Defense protects you
First and foremost, as pioneers in this industry and active researchers, the Source Defense research team ensures that compromised domains are blacklisted in a timely manner, often before even the companies that specialize in identifying and publishing blacklisted domains.
Websites with the Protect product remain secure by:
- Using the “Block New Scripts” configuration.
- Maintaining the default configuration that auto-applies recommended policies — in this case, a block policy would be appliedto the malicious script in a timely manner.
- Applying the recommended policy upon receiving the immediate alert.
Needless to say, websites using the Detect product will also receive an alert in a timely manner, so they can remove the malicious code from their codebase based on the event details in the alert.
How you’d be alerted
If reviewgatherer[.]com or GTM-PQ5XJC53 were to load on a customer site, Source Defense would generate alerts such as the following:
- Accessing PCI or PII fields
- Scripts loaded from a blacklisted domain
- Communication with blacklisted domain
- Data transfer
These alerts appear prominently in the bell notification center, dashboard summaries and on the ‘Found in blacklists’ and ‘Script behaviors’ widgets.
Summary
This attack is a perfect example of why context-aware threats require context-aware defenses. It bypasses URL checks, requires no conditional logic, and hides within routine business content — making it nearly invisible to CSPs or traditional scanning tools.
This attack highlights the need for layered client-side security — from proactive domain intelligence driven by active research, to real-time behavioral detection and the ability to automatically enforce protection policies before damage is done.