TRUSTED CDN ABUSED FOR CREDIT CARD THEFT BY MAGECART SKIMMER
A sophisticated Magecart campaign has been uncovered by the Source Defense Research team, one that pushes the limits of stealth and persistence.
In this attack, the compromise occurs at the server level—malicious code is injected directly into a legitimate first-party JavaScript bundle. Once active, the attack replaces standard payment functionality with a skimmer, capturing customer card data and exfiltrating it via a trusted CDN.
By blending into expected behavior and leveraging infrastructure that security teams typically trust, the attackers achieved a level of invisibility that makes this campaign stand out.
Attack details
The operation was multi-layered, using several techniques in concert to evade detection:
- Injected into a First-Party Script
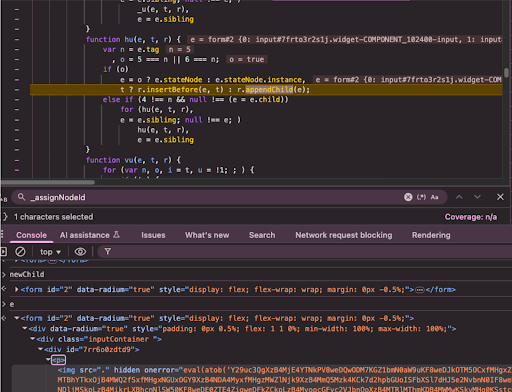
The compromise began at the merchant’s infrastructure level, where malicious code was injected into a legitimate first-party script bundle (elite-bundle.min.js). This script dynamically loaded additional obfuscated code, including a fake form with a broken image. The image’s onerror handler contained an eval function that created the skimmer in memory. - Loading of the Skimmer
The skimmer exploited unusual DOM behavior: payment details were written into the <input> element’s value attribute instead of remaining transient in memory, converting transient card data into persistent HTML, making it easily retrievable by the injected script. - Exfiltration via a Trusted CDN and disguised as Analytics
Once active, the skimmer collected sensitive checkout details by serializing all inputs when the user clicked the payment button. The data was encrypted using a custom AES-CTR implementation and exfiltrated to a Bunny CDN subdomain (b-cdn.net). To avoid suspicion, the exfiltration requests were disguised to look like Google Analytics queries, blending into normal activity and evading traditional anomaly detection.
How Source Defense would protect against this
Source Defense provides runtime protection against this type of advanced client-side threat—even when malicious code is injected into a first-party bundle. Our solution monitors and blocks unauthorized behaviors such as:
- Unexpected DOM manipulation or cloning of HTML elements
- Scripts attempting to serialize and extract PCI or other sensitive data.
- Data transfers to suspicious or previously unseen domains, even when hidden behind trusted CDNs.
Through script isolation and behavior analysis, Source Defense would prevent this attack from capturing or transmitting sensitive data.
How You’d Be Alerted
If this skimmer were present on a Source Defense–protected site, the system would trigger immediate alerts, including:
- New first-party script detected
- Accessing PCI data
- Sending data to blacklisted or suspicious domain
These alerts would be displayed in the dashboard summary, behavior widgets, and notification center, all marked in red for immediate visibility.
Key takeaways
This attack underscores three critical realities:
- First-party code is not immune—server-side compromises can weaponize trusted assets.
- Trusted infrastructure can be abused—using Bunny CDN as an exfiltration channel shows how attackers hide in plain sight.
- Traditional defenses fall short—CSP, WAFs, and blacklist-only tools cannot detect obfuscated payloads that encrypt and disguise data as normal analytics traffic.
A dedicated client-side protection solution like Source Defense is essential to detect, block, and alert on these sophisticated Magecart tactics in real time—before customer data is stolen.