SOPHISTICATED WEBSOCKET ATTACK LEVERAGING BROKEN IMAGES AND SELF-REMOVING JAVASCRIPT
May 27, 2025
The Source Defense Research team has uncovered a highly sophisticated client-side attack employing advanced evasion techniques. This latest campaign leverages broken <img> elements — specifically using their onerror event — to automatically execute obfuscated JavaScript when an image fails to load. Because the payload is injected into an <img> tag that is already broken and hidden, it is trivial for attackers to delete it immediately after execution, leaving minimal forensic trace. The hidden payloads are then used to dynamically execute commands via WebSocket communication, and finally, all traces are removed to evade detection.
The attack chain involves two observed variations connecting to different WebSocket servers:
- wss://dcmplugins[.]com/code/consistency/
- wss://cdn-shopifycs[.]com/telemetry/I04001/
Both exhibit identical obfuscation and execution tactics, strongly suggesting they originate from the same threat actor or toolkit. Critically, the code streamed through these WebSocket connections has been identified as Magecart malware — designed to steal payment data directly from user inputs.
Attack details
1. Entry Vector: Broken Image Injection
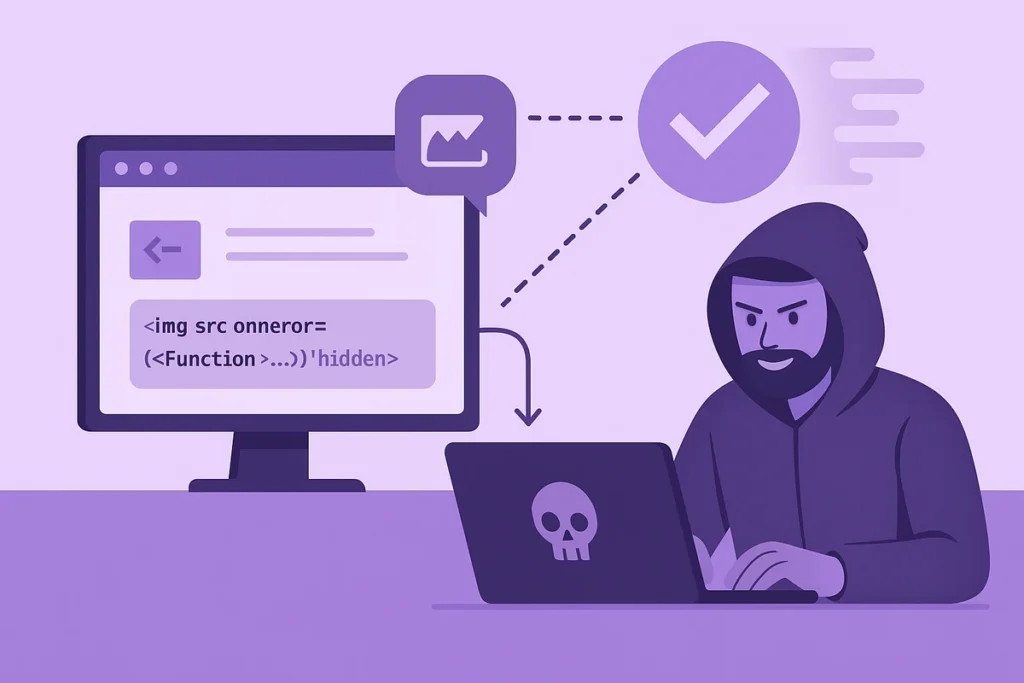
Attackers insert a broken <img> tag containing an onerror attribute, like so:
<img src onerror=”(obfuscated dynamic Function)” hidden>
This technique exploits the browser behavior when handling broken images. Since the src is empty or points to an invalid resource, the browser automatically triggers the onerror event. This event then executes the provided JavaScript, which is typically obfuscated. This method is stealthy and difficult to detect for several reasons:
- It uses a common HTML element (<img>) not typically scrutinized for script behavior.
- The onerror fires automatically, requiring no user interaction.
- The element is hidden from view.
2. Hidden Payload Decoding Techniques
The injected script employs multiple layers of obfuscation:
- Base64 encoding of the core payload.
- String manipulation (splitting, reversing) to further obscure the code.
- XOR ciphering with short keys (e.g., KEPAS, KALPE) to hide the WebSocket endpoints.
This sophisticated approach makes static detection extremely challenging, even for specialized red teams.
3. Real-Time Dynamic Payload Delivery via WebSocket
Upon execution, the malware opens a persistent WebSocket connection to one of the malicious servers. The attacker can then:
- Stream dynamic JavaScript payloads into the victim’s browser.
- Execute code in real-time.
- Adapt attack strategies on the fly, bypassing static signature-based defenses.
4. Auto-Cleanup of Evidence
Immediately after execution, the injected <img> tag self-deletes via:
d.parentNode.removeChild(d);
This “self-cleaning” behavior minimizes the footprint, significantly hindering forensic investigations and automated detection mechanisms.
Key Takeaways
- Advanced evasion: The use of real-time WebSocket payloads and auto-cleanup renders traditional script scanning ineffective.
- Dynamic behavior: Attackers can shift tactics mid-attack without modifying static website code.
- Detection difficulty: Even trained cybersecurity professionals and red teams familiar with the attack might struggle to track the source.
This attack underlines the importance of real-time client-side protection and behavioral monitoring beyond static code analysis.
How does Source Defense protects you
Source Defense’s Protect and Detect products monitor all DOM manipulations, including:
- Creation of suspicious dynamic elements.
- Initiation of unauthorized WebSocket connections.
- Anomalous JavaScript function invocations (e.g., new Function() inside unknown scripts).
If such behavior is detected, automatic block policies are enforced, and alerts are generated for:
- Accessing PCI (Payment Card Information) data.
- Accessing PII (Personally Identifiable Information).
- Sending data to blacklisted domains.
- Executing risky code (e.g., use of new Function() from an untrusted source).
These alerts are prominently displayed in:
- The bell notification center.
- The dashboard summary (highlighted in red).
- The “Found in blacklists” and “Script behaviors” widgets (highlighted in red).
Stay tuned for further updates, and ensure all your sites maintain comprehensive protection across all pages.