SNEAKY SKIMMER STEALS CREDIT CARDS AFTER VALIDATION, DISGUISED AS LEGITIMATE JQUERY LIBRARY
A travel company based in Texas has become the latest victim of a sophisticated Magecart attack, where cardholder data is stolen not by tampering with existing inputs—but by overlaying fake fields that visually mimic them.
The skimmer only activates on checkout pages, collecting and validating credit card data locally before sending it out over WebSockets to attacker-controlled domains.
What makes this attack particularly dangerous is its use of staged exfiltration logic and sequential fallback domains, making it resilient against takedowns and evasive to detection.
Attack details
The attack begins with a malicious loader that only executes on pages containing the string checkout. Once activated, it injects a script named jquery.colors.min.js – masquerading as a legitimate JavaScript library – by base64-decoding its source URL: https://cdn.userghawg[.]info/jquery.colors.min.js?ver=3.0.0. This injected skimmer waits for real payment fields—specifically the #cc-number iframe—to load. It then places three visually overlaid fake input fields on top of the real ones to capture card number, expiration date, and CVC.
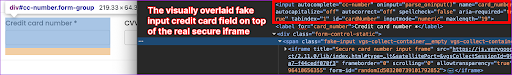
Input is captured, validated locally (including Luhn checks), and stored in localStorage along with a session token. Once the user clicks the checkout button, and only if the data passes validation, the stolen information is sent via WebSocket to the first available of three attacker domains:
- wss://click.userghwg[.]info:2087
- wss://cdn.userghawg[.]info:2083
- wss://style.css-animations[.]online:2096
The WebSocket connection is attempted in order until one succeeds, increasing the chances of successful exfiltration.
How does Source Defense protect against this attack
Source Defense prevents unauthorized client-side script activity by blocking and controlling the behavior of third-party scripts. In this case, the injected loader script and the malicious jquery.colors.min.js would be blocked or prevent them from accessing the PCI fields, thereby neutralizing the skimmer before it has a chance to execute.
How you’d be alerted
Upon detection of any of the attacker-controlled domains or suspicious script behavior—such as fake field injection, WebSocket exfiltration, or access to payment card data—Source Defense would trigger multiple alerts. These include:
If this attack reaches your site, the following alerts are triggered:
- Script load from a blacklisted domain
- Script sends data to a blacklisted domain
- Accessing PCI data
These alerts would surface in the dashboard summary, the bell notification center, and in the ‘Script behaviors’ and ‘Found in blacklists’ widgets.
Key takeaways
This Magecart attack highlights the increasingly evasive and resilient techniques attackers are using, such as fake input overlays, local validation to bypass honeypots, and WebSocket-based exfiltration with domain fallback.
Traditional security tools relying on static blacklists or CSP rules won’t catch such client-side abuse.
A solution for blocking dynamic injection attempts, neutralizing obfuscated loaders, and enforcing runtime script behavior policies is essential, before data can be harvested or leaked.
