RELYING ON EXTERNAL PAYMENT PROVIDERS IS NOT ENOUGH; HUNDREDS OF SUCH SITES ARE UNDER ATTACK
June 24, 2025
Many eCommerces assume they’re safe since they don’t collect payment data; instead users are redirected to trusted providers like Stripe, PayPal and others. An active CosmicSting Magecart variant proves that belief dangerously false.
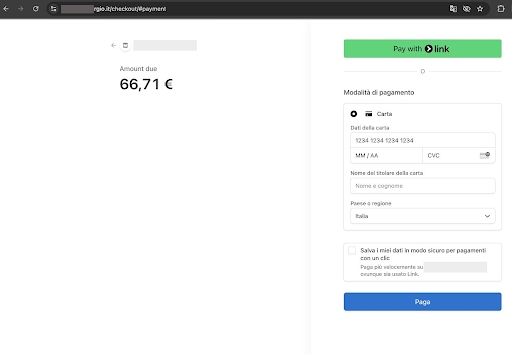
The Source Defense Research Team has observed a persistent variant of the CosmicSting attack that triggers just before redirection to external payment services. Using a fake branded form – see Stripe example below – attackers intercept credentials moments before users reach the legitimate provider.
These forms are designed to be indistinguishable from the real interface and appear at the most opportune time — right when the user thinks they’re safely checking out via a secure third-party gateway. Unfortunately, the real redirect comes too late to prevent the damage.
Even businesses that never store or transmit payment data themselves are exposed. The attack shows that outsourcing payment does not mean outsourcing risk.
CosmicSting campaign sttack details
The broader CosmicSting campaign remains ongoing, despite earlier disclosures. Our research confirms infections on hundreds of websites globally, with attackers using fresh domains — all previously unlisted on major blacklists – to slip past conventional defenses unnoticed.
The communication method continues to leverage WebSocket connections, with the Magecart payload embedded in the very first WebSocket message, further complicating detection.
This technique is especially effective on sites that believe they’re secure because they don’t process payment data directly. But the attack hits just before the protection kicks in — exposing the gap in coverage.
CosmicSting exploits a critical vulnerability — CVE-2024-34102 — which grants unauthorized access to private server files. When paired with the recently exposed Linux iconv bug, this vulnerability may even open the door to remote code execution — a rare and dangerous combination.
Dive deeper into the vulnerability details via our blog:
Critical Security Update for Adobe Commerce / Magento Users
How does Source Defense Keeps You Safe
To protect against these sophisticated techniques, Source Defense provides:
- Ongoing of new domains linked to CosmicSting.
- WebSocket exfiltration monitoring for early detection of client-side threats, under the “Data transfer” script behavior listed.
No matter how you handle payments — in-house or through external services — you must secure the entire client-side environment; otherwise, your site remains exposed and vulnerable.