LIVE ATTACK HIDING BEHIND GOOGLE APPS
March 18, 2025
Content Security Policy (CSP) and similar solutions allow scripts from “trusted” sources to run freely; but what happens when these sources are compromised?
The Source Defense Research Team discovered yet another sophisticated attack that has been active for about a year; this time exploiting Google’s trusted domains to execute malicious scripts.
This attack targets 16 different websites and was discovered on the website of a prominent American food manufacturing company with annual revenues estimated between $100 million and $500 million. Notably, Source Defense previously identified this company under a Magecart attack this past summer. In both instances, Source Defense notified the company of the malicious code, which was subsequently removed.
The malicious script is loaded from a legitimate domain – a Google storage service called Firebase, which is a sub-domain of the googleapis domain. The attack code is neatly placed in different folders for each site targeted. It sends the stolen credit card details to another legitimate domain belonging to a Google service, Cloud Run. However, some of these sub-domains are malicious and even blacklisted by common blacklist vendors. The others were flagged internally by Source Defense, who actively monitor and identify domains exhibiting suspicious activity related to such attacks.
This tactic underscores a significant limitation of Content Security Policies (CSP) and similar security measures that permit scripts from trusted sources without thorough verification and ongoing tracking of the script behavior. When these trusted sources are exploited, traditional CSP configurations won’t suffice to prevent such attacks. Furthermore, the image below shows how this domain was whitelisted via CSP where this attack was active.
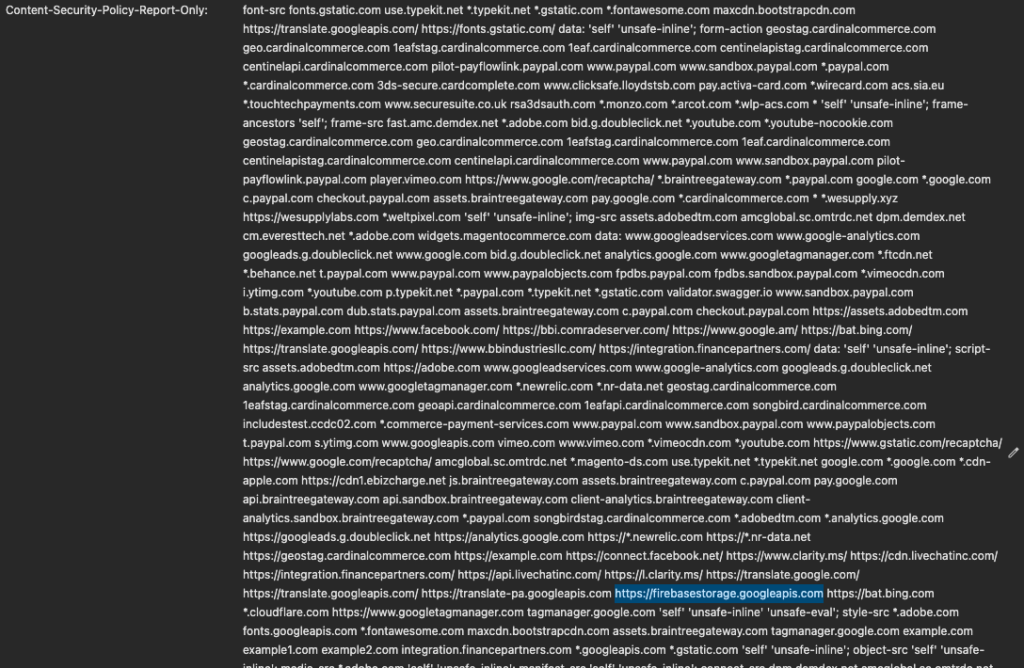
To mitigate these risks, it’s crucial to implement security measures that go beyond standard CSP configurations. Monitoring for unusual script behaviors, validating the integrity of scripts from trusted domains, and actively responding to interactions with blacklisted or suspicious domains and sub-domains are essential steps in defending against such sophisticated threats.
Attack details
The malicious code targets checkout processes by searching for a checkout button on the webpage. Upon detection, it attaches event listeners to input fields to monitor user entries. As users input their payment information, the script captures this data and employs XOR-based encryption to obfuscate the stolen details, aiming to evade detection by cybersecurity researchers. The encrypted payment data is then transmitted to a malicious sub-domain controlled by the attackers.
How does Source Defense protect you from such attacks?
Source Defense offers comprehensive protection against client-side threats through its platform, which includes both detection and protection capabilities. When a script attempts to send data to a blacklisted domain or sub-domain, the platform sends a block policy on that script, effectively preventing unauthorized data transmission.
For customers utilizing the Detect product, the system generates alerts for manual intervention to block the malicious script.
Additionally, the dedicated Professional Services Team proactively contacts affected customers, even those with an auto-accept policy, to ensure appropriate blocking measures are enforced.
How will you be alerted?
Upon detection of a script attempting to send data to a malicious domain, Source Defense issues the following alerts:
- New behaviors identified:
- Accessing PCI data
- Sending data to blacklisted domain
These alerts would be prominently displayed in:
- The bell notification center
- The dashboard summary – marked in red.
- The ‘Script behaviors’ widget will show suspicious activity, accessing PCI data and sending data to blacklisted domain, highlighted in red.