DOUBLE-ENTRY MAGECART CAMPAIGN ADAPTS PER WEBSITE AND LANGUAGE
Source Defense researchers have uncovered a global Magecart campaign that takes localization and deception to a new level. Active across more than 40 e-commerce websites, this operation combines adaptive payloads, counterfeit payment interfaces, and novel exfiltration methods. What makes it especially concerning: the malicious code customizes itself per site and even per language—making detection far more difficult.
Attack overview: Modular, adaptive, and localized
The campaign is launched via a short inline first-party JavaScript snippet that calls out to pubanalytics[.]net when a page URL includes localized keywords like “checkout”, “payment”, “pricing”, or even “penztar” (Hungarian for “checkout”).
Upon activation, the attacker selectively delivers one of several malicious payloads. These payloads are either:
- Hosted on external attacker-controlled domains such as analytic-content[.]com and siteimproveanalytic[.]net, not widely known as malicious domains prior to the Source Defense publication on X.
- Or more covertly, stored directly on the compromised victim’s own domain to evade detection, as it doesn’t require an explicit call to an additional 3rd party script
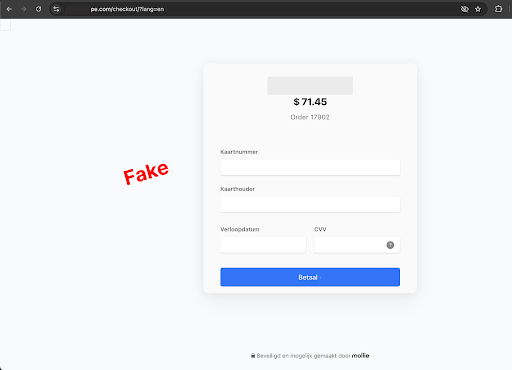
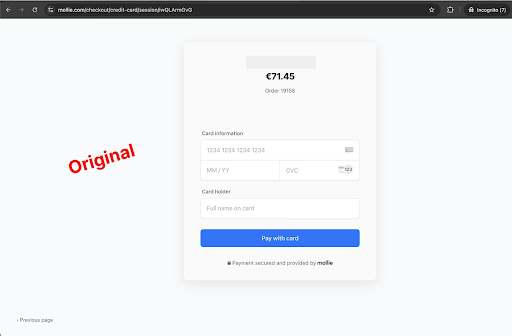
Fake payment interfaces tailored per website
Depending on the victim’s checkout flow and language, the attack dynamically creates counterfeit forms for:
Upon activation, the attacker selectively delivers one of several malicious payloads. These payloads are either:
- PayPal, using deceptive buttons and iframes mimicking the actual payment flow.
- Mollie Payments, faking the full HTML interface.
- Generic branded payment forms—complete with real logos and address autocomplete features.
In every case, these forms are not simply static clones—they’re embedded with site-specific and language-specific logic, making them indistinguishable from legitimate interfaces. On Mexican sites, for example, the attack is only triggered if the page contains the keyword “finalizar”.
WebSocket-based data exfiltration
Once users input their data into these fake forms including credit card details, billing and contact information, this information is sent off via WebSocket connections to attacker domains including:
- lgstd[.]io
- analytic-content[.]com
- In some cases, even back to the victim’s own domain, disguised as image beacon requests
Why this attack stands out
What makes this campaign uniquely concerning:
- Highly adaptable: Behavior varies across websites, mimicking their unique checkout flows.
- Language-aware: Tailored activation based on URL patterns and localized language.
- Uses victim infrastructure: Hosts malicious scripts and exfiltrates data via the victim’s own domain for stealth.
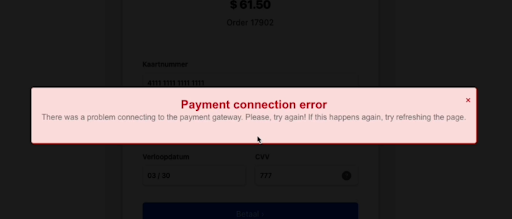
- Dynamic deception: Fake failures trigger re-entry of card data.
How Source Defense protects you
- Behavioral Analysis of 1st and 3rd party scripts: Source Defense alerts of suspicious behaviors such as accessing PCI/PII data from 3rd party scripts and 1st party scripts.\
- Blacklisted and/or unrecognized domain: Due to ongoing research, Source Defense often are first to flag malicious domains identified; regardless, unidentified domains are flagged.
- Automatic Policy Blocking: For Protect customers, malicious domains are immediately blocked. Detect customers receive alerts, enabling rapid manual intervention
How will you be alerted?
When such a threat is active on your website, Source Defense will issue the following alerts:
- New Behaviors Identified:
- Script loading from a blacklisted domain
- Sending data to a blacklisted domain
- Accessing PCI data
- Accessing PII data
These alerts are prominently displayed in:
- The Bell Notification Center
- The Dashboard Summary
- Scripts page — ‘Found in Blacklists’ & ‘Script Behaviors’ widgets (flagged in red)
- Email and webhook event to those who opt in to the respective channel
Key takeaways
- This Magecart campaign is not one-size-fits-all—it adapts per website and per language.
- It uses a mix of third-party and compromised first-party infrastructure to hide in plain sight.
- WebSocket-based data exfiltration makes detection harder for traditional tools.
- Counterfeit payment flows are highly convincing, dynamically swapping between fake and real interfaces.
- Continuous behavioral monitoring and staying on top of latest attacks is essential for defense.
