DOUBLE-ENCODED MAGECART ATTACK HIDES BEHIND LEGITIMATE DOMAIN, IMPACTS OVER 1K WEBSITES
June 10, 2025
First-party script encodes stolen payment data twice, routes it through a trusted Czech eCommerce site
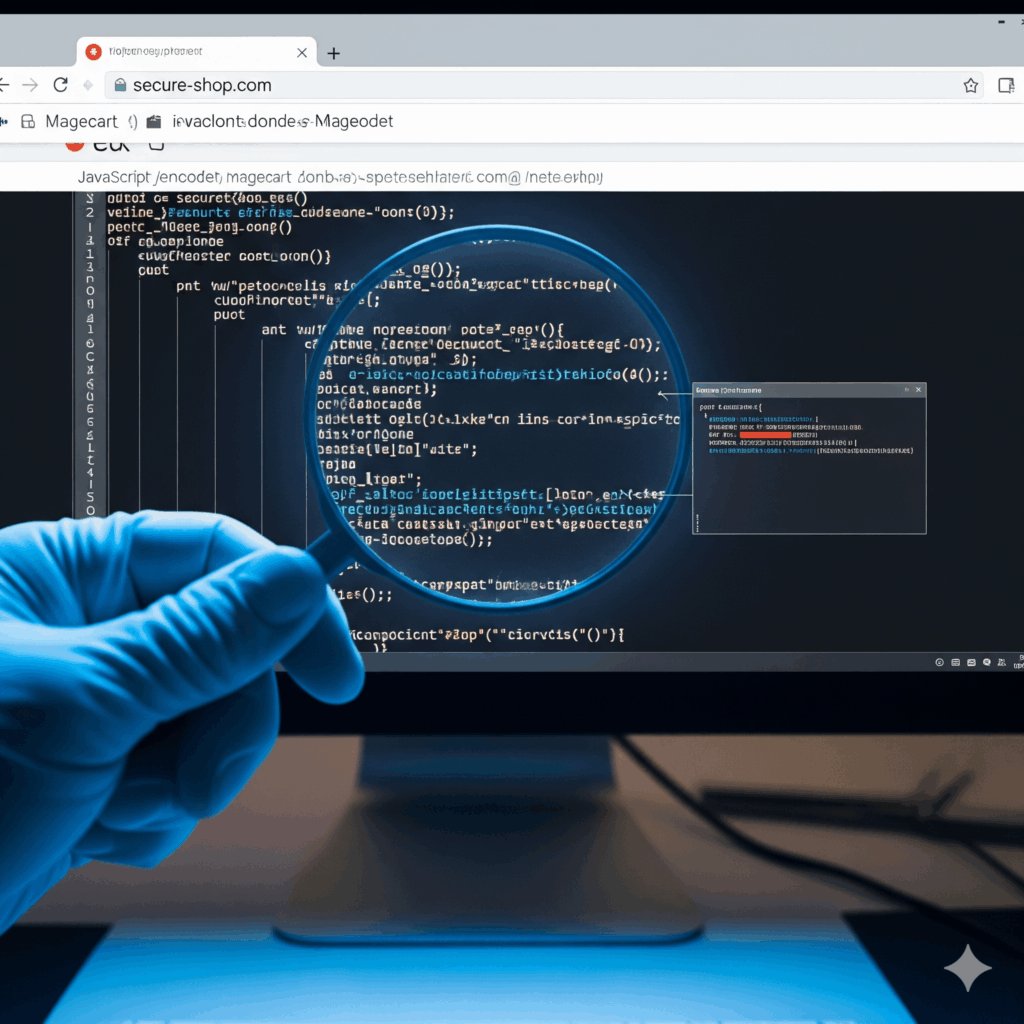
The Source Defense Research Team has uncovered a sophisticated Magecart campaign that has compromised over 1,000 eCommerce websites worldwide. This attack is notable for its use of a first-party script, embedded directly into the merchant’s infrastructure, which imitates legitimate payment workflows to steal sensitive information.
Key findings
- The malicious code is delivered via a heavily obfuscated first-party script.
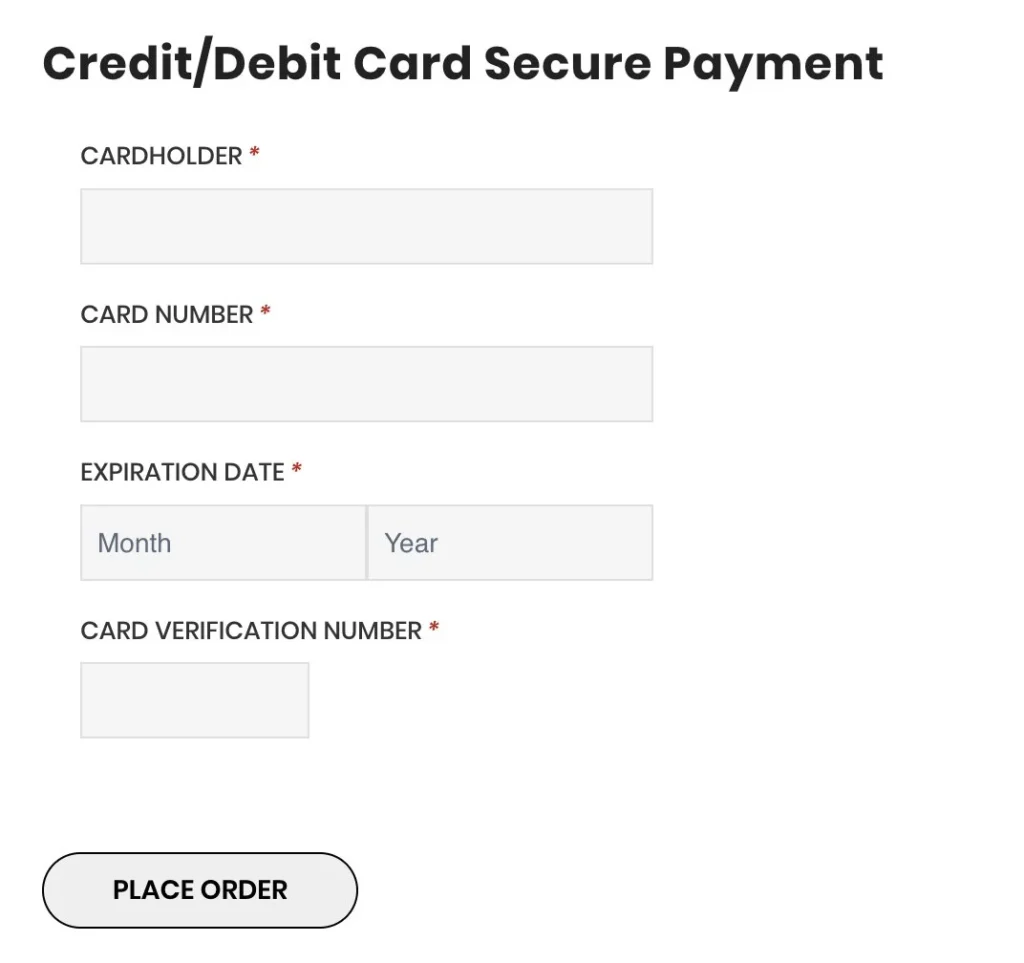
- When a customer fills out the fake payment form (screenshot below), their payment data is:
- Encoded twice—first in HEX, then in Base64—to obscure its true nature.
- Sent to two external domains:
- magentoplugins[.]cc – a known malicious endpoint.
- eshop.instalace-tzb[.]cz – a legitimate Czech eCommerce domain used as a cloaked relay.
This campaign demonstrates an advanced technique where a real, operational website is leveraged to lend credibility and concealment to the attack. Because the second domain is not inherently malicious in appearance, it often bypasses traditional blacklist-based defenses.
Further evading detection, the attackers have implemented a debugging trap that halts execution if developer tools are detected in the browser—frustrating analysis and incident response.
The real danger: hiding behind trust
This isn’t the first instance where Magecart actors have weaponized legitimate infrastructure. Our research has repeatedly identified attacks hosted on, or relayed through, otherwise benign domains. This approach greatly reduces the likelihood of detection while increasing the perceived legitimacy of the data flow.
Because eshop.instalace-tzb[.]cz is still operational and unaffiliated with the attackers, Source Defense has added it to our internal blacklist to ensure our customers are alerted if it appears on their digital properties.
How does Source Defense help?
Since the threat is executed via a first-party script, by design, it’s not possible to block the malicious behavior. However, we proactively detect and alert on anomalous script behavior, even when it originates from a merchant’s own codebase. Customers will be notified of:
- Access to PCI or PII data
- Communications with flagged or newly suspicious domains
Our Professional Services Team actively supports impacted clients with forensic insights and tailored response actions, when needed.