DÉJÀ VU: REUSED GTM HIDES MAGECART WITH NEVER-BEFORE-SEEN OBFUSCATION
A newly discovered Magecart campaign is reusing infrastructure from older attacks; specifically, a Google Tag Manager (GTM) container previously shared on the Source Defense Research X channel. This time, attackers are injecting fake payment forms into live checkout flows, stealing PCI and PII data via a stealthy skimmer that uses WebSocket connections to exfiltrate data in real time, bypassing traditional monitoring tools. Detected on more than 30 unrelated eCommerce sites, the campaign stands out for its novel use of double obfuscation—including one obfuscation method not previously seen in the wild.
Attack details
Attackers compromised GTM containers to inject a JavaScript loader obfuscated using two distinct methods; one of which is a new, never-before-seen obfuscation technique involving reversed strings and XOR logic. Once decoded, the loader constructs a connection to the C2 server at the known malicious WebSocket domain:
wss://jqeury[.]net/jl?source=<page URL>
This campaign relies on two GTM containers:
- GTM-K9KWWGX4 – Previously identified by Source Defense in an unrelated campaign linked to gstatlc[.]org, now repurposed for this new WebSocket attack.
- GTM-T89D4THJ – Appears new and unreported prior to this campaign.
Both containers were active across more than 30 eCommerce websites worldwide, indicating a large-scale, coordinated effort involving both infrastructure reuse and new elements.
Once the WebSocket connects, the real attack begins. A second payload is pushed to the browser that:
- Monitors the page for checkout signals, such as form fields, “Ship Here” buttons, and payment inputs.
- Injects a fake payment form—designed to mimic the look and feel of the host site using normalize.css and site-neutral styling rules.
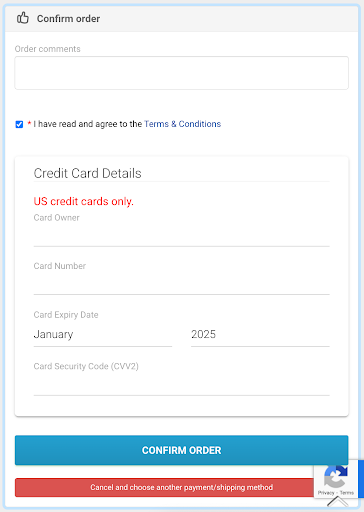
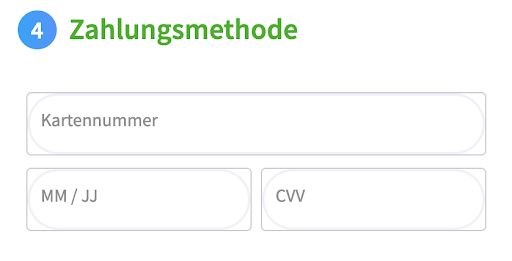
- Overlays or replaces the real form in a double-entry skimming pattern: the user interacts with a realistic but rogue UI that captures inputs and sends them to the attackers.
- Captures data across same-origin iframes, ensuring embedded payment fields aren’t safe either.
The attack stores user input (credit cards, shipping data, form fields) in localStorage, using a queueing system to ensure delivery—even if the user leaves the page mid-session. Exfiltration occurs over the WebSocket using base64-encoded JSON, including session identifiers and browser fingerprinting data.
How does Source Defense protect you
Source Defense protects against this attack on multiple levels:
- Prevents execution of malicious scripts, even when obfuscated or injected via GTM.
- Block access to a sensitive input, including blocking the malicious script from accessing the fake payment form he created.
- Detects suspicious use of risky code such as new Function, that hint at advanced obfuscation and stealth behavior
How you’d be alerted
If this campaign activated on your site, Source Defense would trigger:
- Attempts to access PCI and PII data
- WebSocket communication to a blacklisted domain
Alerts are clearly displayed in the notification center, dashboard summary, and script behavior widgets, with red flags on all suspicious elements.
Key takeaways
This isn’t just another Magecart—it’s a next-generation double-entry attack hiding in GTM and delivering fake forms in real time. The combination of obfuscation, WebSocket channels, and deceptive UIs bypasses traditional defenses like CSP, static script audits, or even fraud monitoring. Without client-side runtime protection, site owners and users alike remain exposed.
Only a real-time, in-browser tool like Source Defense can detect and prevent such attacks – even when hidden behind legitimate tools like GTM.
