With the release of PCI 4.0, comes the recognition that client-side attacks must be on the mind of any organization conducting transactions online. This comes on the heels of multiple years of high-profile attacks impacting many of the world’s largest retailers and millions of consumers.
PCI’s latest guidance, under 6.4.3, makes it clear that you need to be focused on managing and mitigating client-side web application attacks. While currently provided as a best practice, as opposed to a compliance mandate, PCI is signaling its concern that this vector of attack represents a significant and material risk. Although they are giving ample leeway (until 2025) for organizations to get up to speed before mandating compliance, the inclusion of this focus should be seen as a warning for InfoSec teams across the globe that the time to act is now.
It’s been four years since the Payment Card Industry’s last update, and the focus on client-side security couldn’t have come at a better time. With a fundamental shift in consumer buying behaviors leading to an exponential increase in online commerce, client-side web application attacks can only be expected to grow in pace. 2022 has already seen hundreds of attacks — including the high-profile attack on Segway — and given the average client-side attack goes undetected for months, more are sure to be disclosed soon. For any business bound by PCI that takes online payments, it’s essential for you to understand PCI’s guidance under 6.4.3.
What Does PCI 6.4.3 Warn Us About and Why Now?
PCI’s 6.4.3 highlights a major issue in 3rd party risk that you might not currently have on your radar. Your web properties are dynamic and much of the functionality they rely upon comes from a digital supply chain of 3rd, 4th and nth parties which run JavaScript from their own servers (outside of your control), directly into each consumer’s web session. 6.4.3 recognizes this problem and gives you insight into the issue as It states, “Scripts loaded and executed in the payment page can have their functionality altered without the entity’s knowledge and can also have the functionality to load additional external scripts.”
3rd party partners, while vital to the functionality and design of your site, are used as the attack vector for client-side attacks by cybercriminals. It’s extremely likely that your 3rd party partners run 4th and sometimes 5th party scripts on the client-side that are vulnerable to attack from cybercriminals as well. These criminals infiltrate browser sessions to access and steal the sensitive and privacy-protected data you collect from transactions and submission forms on your site.
3rd party scripts are common across industries — especially in organizations that process payment card transactions. According to our report, Third-Party Digital Supply Chain Risk: Exposing the Shadow Code on Your Web Properties, websites that process payment card data, have up to sixteen 3rd parties, and those partners can bring in about 6 total 4th parties. With the average for 3rd party scripts in the double-digits and about half of those partners adding 4th party scripts to the page, PCI is right to draw your attention to strengthening client-side security.
Decoding PCI 6.4.3 Guidance
PCI’s defined guidance for 6.4.3 states:
“All payment page scripts that are loaded and executed in the consumer’s browser are managed as follows:
- A method is implemented to confirm that each script is authorized.
- A method is implemented to assure the integrity of each script.
- An inventory of all scripts is maintained with written justification as to why each is necessary.”
For any organization supporting transactions on its site, it’s important to audit your 3rd party digital supply chain and identify how many 3rd, 4th and nth parties are present. According to our research, the average organization has twelve 3rd party scripts and three 4th party scripts on its site. Take a look at the data below pinpointing, on average, just how many 3rd and 4th party scripts are present on an organization’s site depending on the industry:
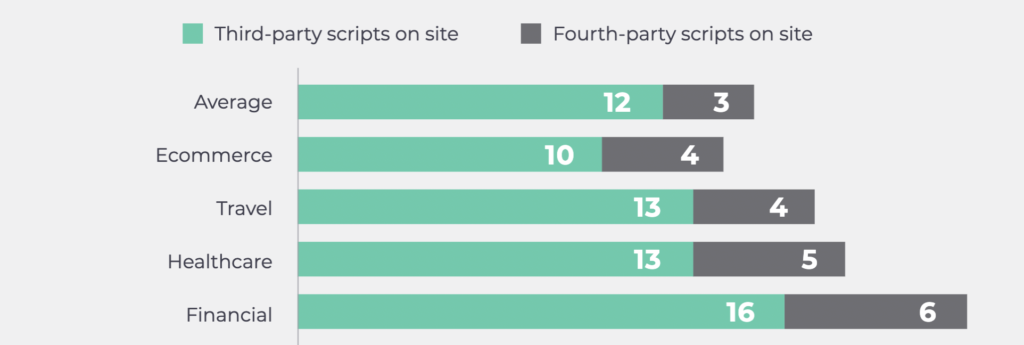
To stay in compliance with PCI 6.4.3 you need to ensure that all parties, including 3rd, 4th, and nth parties, are “authorized” to run on each page of your site. You also need to ensure the integrity and necessity of each script. The dynamic nature of the 4th, 5th, and nth party scripts means reviews and analysis on payment page scripts is a continuous process to ensure PCI compliance.
How Can You Address PCI 6.4.3?
PCI also states, “Unauthorized code cannot be present in the payment page as it is rendered in the consumer’s browser.” This statement raises a few questions:
- So what happens, then, when 3rd or 4th party code is altered on a payment page?
- When does that vendor notify you of the alteration?
- Was the change authorized?
- How long will it take your team to check the validity of the change?
- More importantly, do you have a JavaScript expert on your team to handle these types of investigations?
Alterations to legitimately included scripts on a page can be challenging for even veteran teams to handle. While PCI DSS’ new guidance calls for enhanced visibility over all 3rd and 4th parties, finding the right solution is critically important.
The Source Defense Client-Side Security Platform makes adhering to the guidance in PCI 6.4.3 simple. Firstly, Source Defense gives you full visibility into all scripts running on your web properties… check that box. Secondly, it gives you an incredibly hands-off solution for monitoring the integrity of every script… check that box, too.
Source Defense forces 3rd party scripts to load within a virtual page that is isolated from the client-side. This isolation allows 3rd parties to behave in a controlled environment, enabling Source Defense to permit or deny behavior based on best-in-class security protocols and standardized rules we have in place. As the only purpose-built, patented technology for real-time protection and detection, Source Defense:
- Preserves the end-user experience
- Eliminates unnecessary latency
- Protects the customer journey
Final Thoughts
PCI DSS 6.4.3 is finally addressing the elephant in the room: client-side security. While PCI describes this requirement as “a best practice until 31 March 2025,” the truth is InfoSec teams need to prioritize securing their client-side web applications now. Source Defense can help.
We welcome all questions about PCI DSS 6.4.3 and how Source Defense can keep your organization in compliance. Reach out to us and let’s chat!
