By Source Defense
An authorized IRS eFile website is the latest victim of a JavaScript attack. eFile.com has become the victim of an attack which originated in a previously innocent JavaScript file. The javascript file, popper.js, was modified to include obfuscated code which redirected the browser to a legitimate looking error page. This page enticed a visitor to click a link to update their browser (see error message below). An update.exe file is downloaded and when run, installs a Trojan on the visitors machine.
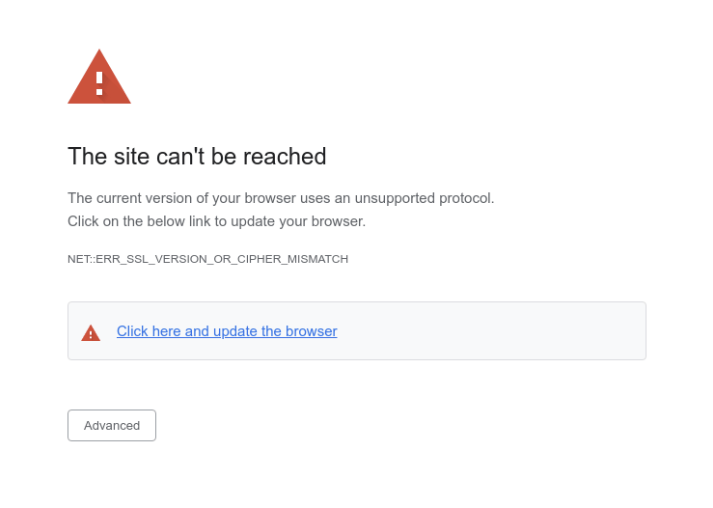
How can this happen?
JavaScript, regardless of origin, has full authority and access on any website it is included in. As a web page is loaded into a browser all JavaScript included in the web page code is executed by the browser and it is at that point that both beneficial and potentially malicious behavior takes place.
Compromising existing JavaScript code is a popular way to bypass technologies like CSP due to the whitelisting nature of this solution. Allowing JS to run on a page so long as its origin remains the same will not prevent modified code from running.
Preventing this attack
For those looking for a hands off solution to this problem, Source Defense Protect will prevent these types of attacks in real time, before any malicious behavior reaches the visitor. Source Defense Protect isolates third party scripts into their own virtual page where a set of rules and access control limits the behaviors JavaScript can perform. Ultimately locking down behaviors to only those that benefit the visitor or website owner.
If you are looking for a more traditional solution, Source Defense Detect uses a combination of signals to monitor for malicious domains, recently created domains, blacklists, and all JavaScript behavior. Events are presented for review in our dashboard with exportable details to keep your teams armed with the information necessary for proper investigation.
Stay vigilant
As the tax filing deadline approaches we encourage you to stay vigilant and, should something not look right, do not use that site until you are sure it is safe.
If you’re looking to protect your own site and its visitors you can request a custom demo at https://sourcedefense.com/request-a-demo/ .
(eFile.com has yet to respond to any inquiries on this attack. All information from sans.edu and this twitter thread)
