Is your website ready for the upcoming holiday spike in online shopping, including Black Friday (November 26 this year) and Cyber Monday (November 29)?
It isn’t until you’ve hardened it against client-side attacks on all the first- and third-party JavaScripts running on it.
Two things are true about this time of year: Hackers love to follow the money, and there will be a lot of it these next few weeks. Those are two strong reasons to find out how to get web app client-side protection for e-commerce on your site.
The big picture looks rosy . . .
Most retailers live and die by their activity in these last couple of months of the calendar year, and the National Retail Federation (NRF) has published some optimistic numbers:
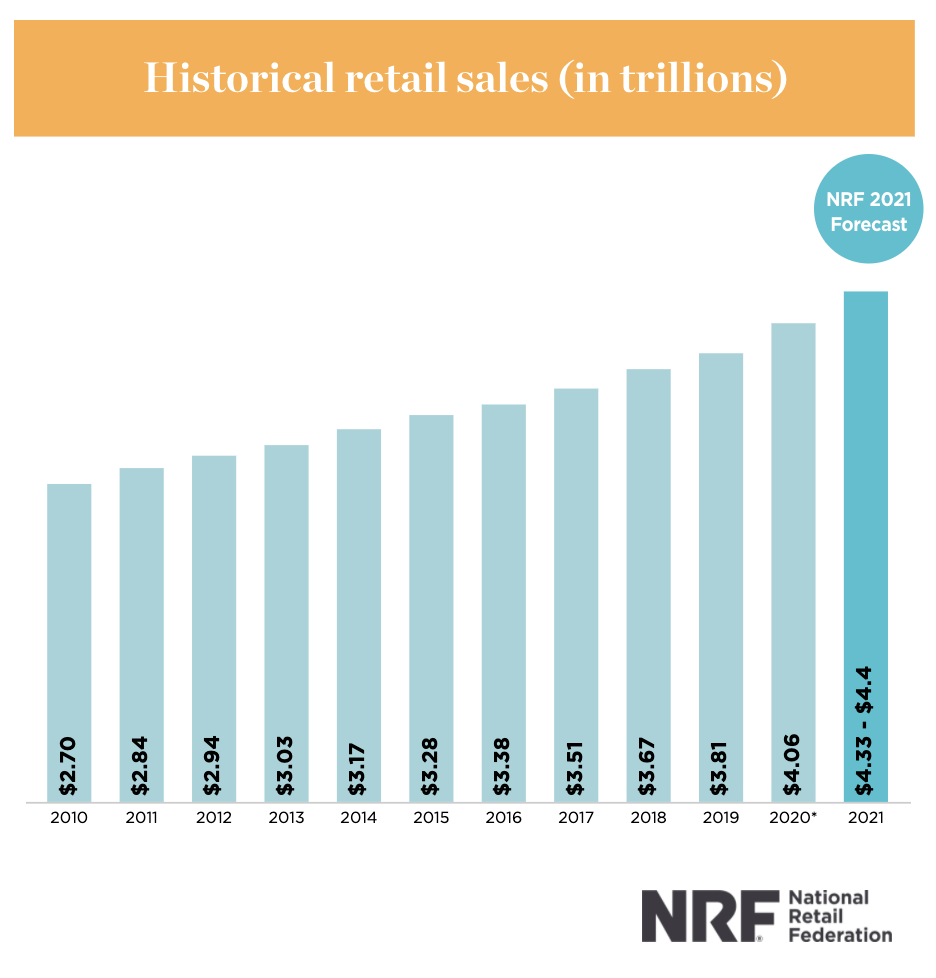
- Even in a pandemic year, the 2020 November-December holiday season was strong in the U.S. Non-store and other online sales represented $206.9 billion in total holiday sales, up 22.6 percent over the year before.
- For all of 2021, online retail sales are expected to grow between 18 percent and 23 percent, to $1.14 – 1.19 trillion.
- As of September 2021, online and other non-store sales were up 0.6 percent month-over-month seasonally adjusted and up 10.5 percent unadjusted year over year.
- For the first nine months of the year, sales as calculated by NRF were up 14.5 percent over the same period in 2020.
In other words, expect your servers to get warm and stay warm through the holidays.
. . . but you may have problems in two supply chains
The headlines are focused on snags in the traditional supply chain, due to global logistics. The pandemic froze a lot of worldwide commerce in its tracks, and restarting all the manufacturing and transport is taking months. That may affect your ability to fulfill orders and deliver on time this holiday season.
The digital supply chain, however, radiates out from your website to third-, fourth- and even fifth-parties. Your e-commerce depends on that supply chain to deliver content, gather customer data and provide functions like tracking, content delivery, authentication and communication. It uses JavaScripts from third-party vendors to deliver services to the customers who will make holiday purchases on your website.
One big difference is that it’s harder to see the digital supply chain than it is to see the traditional supply chain.
That’s not the only difference.
- The traditional supply chain is mature, slow and secure. Shipping practices have been around for centuries, and after days or weeks in transit, loads are subject to inspection by customs officers and freight managers.
- The digital supply chain is immature, fast and insecure. E-commerce has been a serious economic force for less than a generation, and JavaScript can circle the globe within seconds. Your site doesn’t inspect it when it arrives, and any .js file called by your website’s HTML gets full access.
The high cost of JavaScript vulnerabilities
Unfortunately, you’re not the only one who is looking forward to big business at this time of year. Hackers are too, and their Magecart malware and JavaScript exploits are part of a digital supply chain problem that’s hard for you to see. Even if hackers occasionally sleep, the Magecart malware and crooked third-party JavaScript they smuggle onto your website through the digital supply chain never rest.
If a Magecart attack like digital skimming, formjacking or credential harvesting plants malicious, third-party JavaScript on your website, your customers won’t know. They’ll think everything looks normal and continue entering their payment information and personally identifiable information (PII). The transactions will proceed as usual, except that the attackers will get the same information you get.
Eventually, you’ll find out about the attack. Even though you didn’t know it was going on, you’ll be liable for not having done enough to protect the privacy of your customers. You’ll spend a lot of time and money dealing with the damage to your business and reputation. And, of course, your customers will be vexed when you announce the retail breach and they have to start canceling credit cards and blocking identity theft.
Avoid your Magecart nightmare before Christmas
You don’t want problems in both supply chains hanging over all your web transactions during the high-revenue holiday season. And — not to put too fine a point on it — you will not be happy dealing with a Magecart attack in the middle of the holidays, or cleaning up from one afterward.

Of course, there’s not much you can do about the scores of container ships stuck at sea, waiting to unload hundreds of thousands of containers. We can’t help you with the traditional supply chain.
But you can protect yourself against JavaScript exploits in your digital supply chain, and Source Defense can help you.
Unlike an attack, the cost of protecting yourself does not break the bank. Deployment is quick and it adds no complexity to your already strained security operations. Customers report that overall site performance actually improves with JavaScript sandboxing from Source Defense.
Request a demo to find out more about the Source Defense approach to web app client-side protection of your customers’ sensitive data.
