An application firewall is a security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. It is designed to protect a website or application from various types of attacks, such as SQL injection, cross-site scripting, and malware injection.
Application firewalls are typically implemented at the application layer of the OSI model, which is a structure for how different devices communicate in a network. This allows the firewall to monitor and control traffic specific to the application rather than just at the network level.
Application firewalls can be hardware-based, software-based, or a combination of both. They may be configured to block certain types of traffic or to allow only certain types of traffic to pass through.
In addition to protecting against attacks, application firewalls can also be used to monitor and control access to specific features or functions within an application. This can be useful for enforcing security policies or complying with regulatory requirements.
Overall, an application firewall is an important tool for protecting the security and integrity of a website or application.
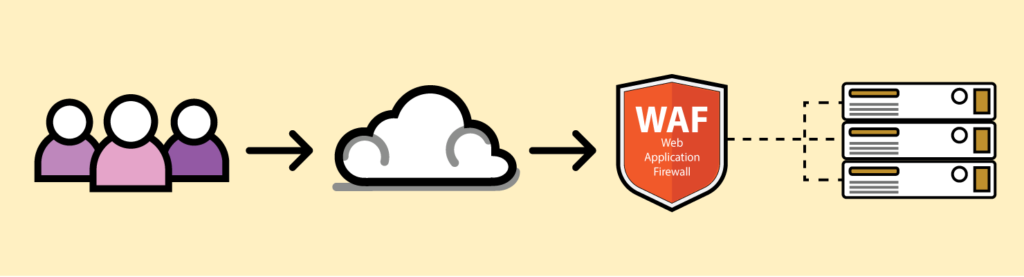
Web Application Firewall (WAF)
One type of application firewall is a web application firewall which is specifically designed for HTTP applications. WAFs are expected to protect web applications from a few types of attacks, including injection attacks and application layer denial of service (DoS). They are generally deployed in front of web servers, protecting web apps from internal and external threats.
WAFs are often used as an additional layer of security in conjunction with other security measures, such as intrusion detection systems and intrusion prevention systems. They can be an effective way to protect a website or web application from a wide range of threats, including those that are targeted specifically at web-based applications.
What is the current state of web application security?
Web application security is an ongoing concern for businesses, organizations, and individuals who rely on the internet for their operations. As more and more sensitive data is transmitted and stored online, the risk of security breaches and data leaks increases.
Many different factors contribute to the current state of web application security. Some of the key issues include the following:
- Increasing sophistication of attacks: Hackers and cybercriminals are constantly developing new tactics and techniques to compromise web applications and steal sensitive data. This includes the use of advanced malware and exploit kits, as well as tactics like phishing and social engineering.
- Lack of security awareness: Many organizations and individuals do not prioritize web application security and may not have sufficient safeguards in place to protect against attacks. This can leave them vulnerable to compromise.
- Outdated software and infrastructure: Many web applications are built on outdated software and infrastructure, which may have known vulnerabilities that attackers can exploit.
- Insufficient testing: Many web applications are not adequately tested for security vulnerabilities before deployment. This can leave them vulnerable to attack once they are deployed.
Overall, the current state of web application security is a concern, and it is important for organizations and individuals to take steps to protect themselves from potential threats. This includes implementing appropriate security measures, regularly updating software and infrastructure, and educating users about the importance of security.